Shortcuts on Keyboard
When speed counts, the keyboard is still king. Almost all the actions and commands you can perform with a mouse you can perform faster using combinations of keys on your keyboard. These simple keyboard shortcuts can get you where you want to go faster than several clicks of a mouse. You'll work faster on spreadsheets and similar documents, too, because you won't lose your place switching back and forth between mouse and keys.
Here are some of the most useful keyboard shortcuts:
Copy. CTRL+C
Cut. CTRL+X
Paste. CTRL+V
Undo. CTRL+Z
Delete. DELETE
Delete selected item permanently without placing the item in the Recycle Bin. SHIFT+DELETE
Copy selected item. CTRL while dragging an item
Create shortcut to selected item. CTRL+SHIFT while dragging an item
Rename selected item. F2
Move the insertion point to the beginning of the next word. CTRL+RIGHT ARROW
Move the insertion point to the beginning of the previous word. CTRL+LEFT ARROW
Move the insertion point to the beginning of the next paragraph. CTRL+DOWN ARROW
Move the insertion point to the beginning of the previous paragraph. CTRL+UP ARROW
Highlight a block of text. CTRL+SHIFT with any of the arrow keys
Select more than one item in a window or on the desktop, or select text within a document. SHIFT with any of the arrow keys
Select all. CTRL+A
Search for a file or folder. F3
View properties for the selected item. ALT+ENTER
Close the active item, or quit the active program. ALT+F4
Opens the shortcut menu for the active window. ALT+SPACEBAR
Close the active document in programs that allow you to have multiple documents open simultaneously. CTRL+F4
Switch between open items. ALT+TAB
Cycle through items in the order they were opened. ALT+ESC
Cycle through screen elements in a window or on the desktop. F6
Display the Address bar list in My Computer or Windows Explorer. F4
Display the shortcut menu for the selected item. SHIFT+F10
Display the System menu for the active window. ALT+SPACEBAR
Display the Start menu. CTRL+ESC
Display the corresponding menu. ALT+Underlined letter in a menu name
Carry out the corresponding command. Underlined letter in a command name on an open menu
Activate the menu bar in the active program. F10
Open the next menu to the right, or open a submenu. RIGHT ARROW
Open the next menu to the left, or close a submenu. LEFT ARROW
Refresh the active window. F5
View the folder one level up in My Computer or Windows Explorer. BACKSPACE
Cancel the current task. ESC
SHIFT when you insert a CD into the CD-ROM drive Prevent the CD from automatically playing.
Use these keyboard shortcuts for dialog boxes:
Move forward through tabs. CTRL+TAB
Move backward through tabs. CTRL+SHIFT+TAB
Move forward through options. TAB
Move backward through options. SHIFT+TAB
Carry out the corresponding command or select the corresponding option. ALT+Underlined letter
Carry out the command for the active option or button. ENTER
Select or clear the check box if the active option is a check box. SPACEBAR
Select a button if the active option is a group of option buttons. Arrow keys
Display Help. F1
Display the items in the active list. F4
Open a folder one level up if a folder is selected in the Save As or Open dialog box. BACKSPACE
If you have a Microsoft Natural Keyboard, or any other compatible keyboard that includes the Windows logo key and the Application key , you can use these keyboard shortcuts:
Display or hide the Start menu.
Display the System Properties dialog box. +BREAK
Show the desktop. +D
Minimize all windows. +M
Restores minimized windows. +Shift+M
Open My Computer. +E
Search for a file or folder. +F
Search for computers. CTRL+ +F
Display Windows Help. +F1
Lock your computer if you are connected to a network domain, or switch users if you are not connected to a network domain. + L
Open the Run dialog box. +R
Display the shortcut menu for the selected item.
Open Utility Manager. +U
Helpful accessibility keyboard shortcuts:
Switch FilterKeys on and off. Right SHIFT for eight seconds
Switch High Contrast on and off. Left ALT +left SHIFT +PRINT SCREEN
Switch MouseKeys on and off. Left ALT +left SHIFT +NUM LOCK
Switch StickyKeys on and off. SHIFT five times
Switch ToggleKeys on and off. NUM LOCK for five seconds
Open Utility Manager. +U
Keyboard shortcuts you can use with Windows Explorer:
Display the bottom of the active window. END
Display the top of the active window. HOME
Display all subfolders under the selected folder. NUM LOCK+ASTERISK on numeric keypad (*)
Display the contents of the selected folder. NUM LOCK+PLUS SIGN on numeric keypad (+)
Collapse the selected folder. NUM LOCK+MINUS SIGN on numeric keypad (-)
Collapse current selection if it's expanded, or select parent folder. LEFT ARROW
Display current selection if it's collapsed, or select first subfolder. RIGHT ARROW
Shortcuts on Keyboard
Posted at Monday, June 30, 2008Trick If You Won't Yahoo Tracking You
Posted at Monday, June 30, 2008Trick If You Won't Yahoo Tracking You
Yahoo! has hidden this option way deep inside somewhere but I'm declaring it here in case there are people who want it anyway
1) Go to the address http://privacy.yahoo.com/privacy & click the "Cookies" link under the "Special Topics" column.
2) Click the "Web Beacons" link under the "Reference Links" Column.
3) On this page, click the "click here to opt out" link toward the end of the third paragraph under the "Outside the Yahoo! Network" title.
4) After a while, a page that says you have been out of the monitoring program will load. Without doing anything, close that page or continue your usual urfing by typing another address in the address bar. (Do NOT click the "Cancel Opt-out" button, your action will be cancelled!).
5) You're done! Now Yahoo! will not record what you're doing during surfing.
Note : How Innocent it may appear but its Voilation of yahoo Policies.
Know How Firewall
Posted at Monday, June 30, 2008Know How Firewall
A firewall is basically something that protects the network from the Internet. It is derived from the concept of firewalls used in vehicles which is a barrier made of fire resistant material protecting the vehicle in case of fire. Anyway a firewall is best described as a software or hardware or both Hardware and Software packet filter that allows only selected packets to pass through from the Internet to your private internal network. A firewall is a system or a group of systems which guard a trusted network( The Internal Private Network from the untrusted network (the Internet.) To understand how a firewall works, firstly we need to understand how exactly data is transferred on the Internet.
The TCP\IP suite is responsible for successful transfer of data across a network both the Internet and the Intranet. The TCP\IP suite is a collection of protocols which are inter-related and interdependent and act as a set of rules according to which data is transferred across the network. A protocol can be defined as a language or a standard which is followed while transfer of data takes place.
A firewall relies on the source and destination IP and also the ports to control the packet transfer between the untrusted network and the trusted network. Firewalls can be classified into 3 types:
1. Packet Filter Firewalls
2. Application proxy Firewalls
3. Packet Inspection Firewalls
Packet Filter Firewalls
They are the earliest and the most criticized firewalls, which nowadays are not easily found. They are usually Hardware based i.e. Router Based (a router is a piece of device which connects two
networks together.) Whenever a Packet Filter Firewall receives a packet for permission to pass through, it compares the header information i.e. the source and destination IP address, and port number with a table of predefined access control rules If the header information matches, then the packet is allowed to pass else the packet is direct contact between the untrusted system and the trusted private system.
Such Firewalls can be fooled by using techniques like IP Spoofing in which we can change the source IP such that the firewall thinks that the packet has come from a trusted system which is among the list of systems which have access through the firewall.
Application proxy Firewalls
The shortcomings of the packet filter firewalls are addressed by the new type of firewalls developed by the DARPA. It was widely believed that the earlier type of firewalls were not secure enough as they allowed the untrusted systems to have a direct connection with the trusted systems. This problem was solved with the use of Proxy servers as firewalls. A proxy server which is used as a firewall are called application proxy servers. This kind of a proxy firewall examines what application or service (running on ports) a packet is meant for and if that particular service is available only then is the packet allowed to pass through and if the service is unavailable then the packet is discarded or dropped by the firewall.
Packet Inspection Firewalls
It can be also known as an extension of the Packet Filter Firewall. It not only verifies the source and
destination IP's and ports, it also takes into consideration or verifies that content of the data before passing it through. There are two ways in which this kind of a firewall verifies the data to
be passed:
State and Session.
In case of state inspection, an incoming packet is allowed to pass through only if there is a matching outward bound request for this packet. This means that the incoming packet is allowed to pass through only if the trusted server had requested for it or had sent an invitation for it.
In case of session filtering, the data of the incoming is not verified, but instead the network activity is traced and once a trusted system ends the session, no further packets from that system pertaining to that session are allowed to pass through.
All along you will come across many Firewalls on various systems, basically a
firewall can be established
or setup in two ways:
1. Dual-homed gateway
2. Demilitarized zone (DMZ)
In a dual homed gateway firewall, there is a single firewall with 2 connections, one for the trusted network and the other for the untrusted network.
In the case of a Demilitarized Firewall or a DMZ there are two firewalls, each with two connections, but there is a slight difference in the case of a DMZ setup.
In the case of a DMZ setup, there are two firewalls, the first having two connections, one leading to the untrusted network and the other leading to the host systems like the email server or the FTP server etc.
In the case of a Dual Homed Gateway the untrusted network is connected to the host systems (email and FTP servers etc) through a firewall and these host systems are connected to the internal private network. There is no second firewall between the host systems and the internal
private trusted network.
The basic structure of the DMZ setup declares it to be a more secure system as even if an attacker gets through the first firewall, he just reaches the host systems, while the internal network is protected by another firewall.
Hacking Into a Computer (used Windows XP Home Edition)
Posted at Monday, June 16, 2008Hacking Into a Computer (used Windows XP Home Edition)
For this tutorial, I used Microsoft’s Windows XP Home Edition OS.
-What is it?-
NetBIOS Hacking is the art of hacking into someone else’s computer through your computer. NetBIOS stands for “Network Basic Input Output System.” It is a way for a LAN or WAN to share folders, files, drives, and printers.
-How can this be of use to me?-
Most people don’t even know, but when they’re on a LAN or WAN they could possibly have their entire hard drive shared and not even know. So if we can find a way into the network, their computer is at our disposal.
-What do I need?-
1) Windows OS
2) A Small hacking tool (Download from here)
Part 1, Finding the target
So first off we need to find a computer or the computer to hack into. So if your plugged in to the LAN, or connected to the WAN, you can begin. Open up Cain and Abel. This program has a built in sniffer feature. A sniffer looks for all IP addresses in the local subnet. Once you have opened up the program click on the sniffer tab, click the Start/Stop sniffer, and then click the blue cross
Another window will pop up, make sure “All host in my subnet” is selected, and then click ok.
It should begin to scan.
Then IP’s, computer names, and mac addresses will show up. Now remember the IP address of the computer you are going to be breaking into. If you can’t tell whether the IP address is a computer, router, modem, etc, that’s ok. During the next step we will begin our trial and error.
Part 2, Trial and Error
Now, we don’t know if we have our designated target, or if we have a computer or printer, or whatever else is on the LAN or WAN. If you did get the IP of the target though, I still recommend reading through this section, for it could be helpful later on. Click on the start menu and go to run, type in cmd, and click ok. This should bring up the command prompt. From here we will do most of the hacking. Now I will be referring to certain commands that need to be inputted into the command prompt. I will put these commands in quotes, but do not put the quotes in the code when you type it into the prompt. I am only doing this to avoid confusion. Let’s get back to the hacking. Type in “ping (IP address of the target).” For example in this tutorial, “ping 192.168.1.103.” This will tell us if the target is online. If it worked, it will look something like this (note, I have colored out private information):
IF it didn’t work, meaning that the target is not online, it will look something like this:
If the target is not online, either switch to a different target, or try another time. If the target is online, then we can proceed.
Part 3, Gathering the Information.
Now, input this command “nbtstat –a (IP address of target).” An example would be “nbtstat –a 192.168.1.103.” This will show us if there is file sharing enabled, and if there is, it will give us the: currently logged on user, workgroup, and computer name.
Ok, you’re probably wondering, “What does all this mean to me?” Well, this is actually very important, without this, the hack would not work. So, let me break it down from the top to bottom. I will just give the first line of information, and then explain the paragraph that follows it.
The information right below the original command says: “Local Area Connection,” this information tells us about our connection through the LAN, and in my case, I am not connected through LAN, so the host is not found, and there is no IP.
The information right below the “Local Area Connection,” is “Wireless Network Connection 2:” It gives us information about the connection to the target through WAN. In my case I am connected through the WAN, so it was able to find the Node IpAddress. The Node IpAddress is the local area IP of the computer you are going to break into.
The NetBIOS Remote Machine Name Table, give us the workgroup of our computer, tells us if it is shared, and gives us the computer name. Sometimes it will even give us the currently logged on user, but in my case, it didn’t. BATGIRL is the name of the computer I am trying to connect to. If you look to the right you should see a <20>. This means that file sharing is enabled on BATGIRL. If there was not a <20> to the right of the Name, then you have reached a dead end and need to go find another IP, or quit for now. Below BATGIRL is the computers workgroup, SUPERHEROES. If you are confused about which one is the workgroup, and the computer, look under the Type category to the right of the < > for every Name. If it says UNIQUE, it is one system, such as a printer or computer. If it is GROUP, then it is the workgroup
Step 4, Breaking In
Finally it’s time. By now we know: that our target is online, our target has file sharing, and our target’s computer name. So it’s time to break in. We will now locate the shared drives, folders, files, or printers. Type in “net view (IP Address of Target)”
An example for this tutorial would be: “net view 192.168.1.103”
We have our just found our share name. In this case, under the share name is “C,” meaning that the only shared thing on the computer is C. Then to the right, under Type, it says “Disk.” This means that it is the actual C DISK of the computer. The C DISK can sometimes be an entire person’s hard drive.
All's that is left to do is “map” the shared drive onto our computer. This means that we will make a drive on our computer, and all the contents of the targets computer can be accessed through our created network drive. Type in “net use K: (IP Address of Target)(Shared Drive). For my example in this tutorial, “net use K: 192.168.1.103C.” Ok, let’s say that you plan on doing this again to a different person, do u see the “K after “net use?” This is the letter of the drive that you are making on your computer. It can be any letter you wish, as long as the same letter is not in use by your computer. So it could be “net use G...,” for a different target.
As you can see, for my hack I have already used “K,” so I used “G” instead. You may also do the same for multiple hacks. If it worked, it will say “The command completed successfully.” If not, you will have to go retrace you steps. Now open up “my computer” under the start menu, and your newly created network drive should be there.
Now, if you disconnect from the WAN or LAN, you will not be able to access this drive, hence the name Network Drive. The drive will not be deleted after you disconnect though, but you won’t be able to access it until you reconnect to the network. So if you are doing this for the content of the drive, I recommend dragging the files and folders inside of the drive onto your computer, because you never know if the target changes the sharing setting. If you are just doing this to hack something, then go explore it and have some well deserved fun!
Congratulations! You’re DONE!
-Commands used in this tutorial:
Code:
PING
NBTSTAT -a (IP Address of Target)
NET VIEW (IP Address of Target)
NET USE K: (IP Address of Target)(SHARENAME)
Increase Printer's Lifespan
Posted at Monday, June 16, 2008Increase Printer's Lifespan
Did you know that color printers have a lifespan that’s perfectly acceptable for both personal and professional use at the price they come, even while laser printers generally last a bit longer? Basically, you end up replacing inkjet printers every three to four years, but laser printers generally last a few years longer. Some users have reported a handful of personal grade laser printers that have been churning out pages for a full decade. Wow! But no matter what kind of printer you use, here are a few tips that will help you maintain your printer in tip top shape for as long as possible!
Tip 1: Go Easy on a Paper Jam
In case of a paper jam, never force the paper out. This can not only damage the printer, but also leave bits of torn paper inside, which could cause harm later on. To get the paper out smoothly, most printers have a hatch attached at the back that can be easily removed. Once this hatch is removed, you will gain access to the paper wheels and you should be able to see the jammed paper to get it out.
Tip 2: Avoid Shutting Down the Printer in an Improper Manner
Turn off your printer when not in use. This can prevent drying of ink and it also helps to keep the printer functioning at an optimum level. Remember to use the printer’s power button and then remove the plug if need be. Don’t turn the power off if you are in the middle of something.
Tip 3: Avoid Cheap Toner/Ink Cartridges
Often times, we are tempted to use either compatible, refilled or remanufactured ink/toner cartridges, which is something we all should avoid. That is like buying a compatible spare part for a car instead of buying the original parts. It may somewhat perform the same function as the original, but it would not last as long and it could affect the performance of the vehicle itself. In addition, we need to look at how such companies manufacture their products. In the case of remanufacturing cartridges, what actually happens is this: the manufacturer would first purchase empty toner cartridges from end users. They would then strip the toner cartridge to its bare minimum and they would then reassemble them after a little bit of cleaning. The area of specific concern here is the toner drum. There is a set lifespan for this item and no amount of cleaning would extend it.
Avoid using cheap toner cartridges and use ones like the one in the screenshot above.
And finally, the lifespan of a printer depends on the sturdiness of the machine, how much you use it and how well you maintain it. Printers will eventually fail, but some will last nearly forever. Take good care of your printer and it will take care of you, for a much longer time. And one more thing: to ensure your printer has a long lifespan, you should not base your purchase solely on its speed or its price. The monthly duty cycle indicates the maximum number of pages the printer is designed to produce. Buying a printer that has a duty cycle that is two to three times your expected print volume will help ensure its longevity as well.
Sidebar: Lifespan of Cartridges
The lifespan of an ink cartridge varies, depending on how often and how much you print. Light users might replace their ink two or three times a year, while heavier users may go through cartridges every few months (cartridges left sitting for a year or more may dry out as well). If you want a more concrete answer on how many pages you’ll get out of a cartridge, consult the manufacturer for the rating on a specific model printer and cartridge. A typical answer will be something along the lines of 350 pages at a five percent coverage. That means a cartridge can print 350 pages with an average of a five percent surface area inked on each page.
The lifespan of a toner cartridge varies greatly, depending on the type of laser printer you have. Cheaper toner cartridges cost under $100 and output 2,500 to 5,000 pages. More expensive toner cartridges are meant for printers that do a lot of printing (a very common reason to have a laser printer in the first place) and will yield tens of thousands of pages. Some of the most expensive, heavy duty cartridges will even yield hundreds of thousands of pages. It just depends on what you buy!
Happy printing!
Penis Enlargement
Posted at Monday, June 16, 2008One of the most effective non-surgical penis health products is the penis extender. There are recommended product of the penis extender such as X4 Labs Penis Extender, Euro Extender and Pro Extender. This penis enlargement device has been effective in treating multiple penis disorders ranging from penile curvature to erectile dysfunction. The medically certified penis enlarger is used and prescribed by renowned doctors worldwide and is a safe non-surgical solution for bent penis, Peyronie’s, erectile dysfunction and permanently increasing the size of the penis.
One of the latest crazes in male enhancement and penis enlargement products is the X4 Labs™ Penis Extender. Replacing the antiquated penis enlargement pump, the X4 Labs™ penis extender was engineered to provide a multitude of benefits ranging from enhancement, enlargement, and correction of certain penile disorders. The X4 Labs™ Extender uses the bodies’ natural ability to adapt, by applying small amounts of force to the penis body skin is forced to regenerate.
After using the EuroExtender™ penis enlargement system you feel that the Comfort Strap is more comfortable and provides better results that silicone tube or noose type penis extenders. If you are already a user of a “noose” type extender, the EuroExtender™’s conversion kit may interest you. It provides better blood circulation, more comfort and better results in a shorter time period.
The Pro Extender is essentially a traditional penis extender, that means the ProExtender™ uses a thin silicone band to secure the penis in place. Some men do find this method more comfortable, however; prior experiences with the device, indicate that the wider strap, such as the X4 Labs™ Penis Extender, is not only more efficient but also more comfortable.
Tutorial Undetectable Remote Hacking
Posted at Monday, June 16, 2008Tutorial Undetectable Remote Hacking
In this tutorial you will learn how to hack a computer any where in the world. Ok well not anywhere obviously things like the military and the goverment will have very high security so you definately wont be able 2 hack them using this method. I hope not aniways =.
A Major Notice If you are behind a router you will need to port forward your router. To do this you can use a DMS. Its hard to explain as every router has a different interface ( homepage that has a different layout ) so i suggest you go to google and search portforward.com. It will teach you how to port forward your router there.
Ok to begin with you will need these three tools : -
Daemon Crypt - http://rapidshare.com/files/8161346/Daemon_Crypt.rar
Pc Guard - http://rapidshare.com/files/11136172/PC_GUard.rar
Yuri Rat - http://rapidshare.com/files/8161510/Yuri_Rat.rar
Ok now that you have these three tools your 1st step will be to open up Yuri Rat and then click on server build
You should now have the following the screen
In this screen I want you to put your IP address into the DNS/IP section.
To get IP Address go to Start > Run > Type CMD and hit enter. When the black box appears type in IPCONFIG. You will then have your IP Address
Port: You Can Leave As Default (-7898-)
Assigned Name: Doesn’t effect how the server will work its just to keep you more organized so if you wanted to hack your friend “JOE” and specifically make this server for him then you may want to type something like “JOES TROJAN”.
Server Install Name: You should leave this as default as I myself don’t know what the difference is as every server you make is named server when it is 1st created anyway. Do not change it as it may make problems but I am not sure.
Ok as you can see there are more settings on the right hand side. I am going to recommend you settings for different purposes
To Hack A Friend For Fun: Uncheck Everything Unless You Want To Do Optional
(OPTIONAL) Melt Server - Your server will disappear into another folder
(OPTIONAL) Custom Icon if you want to make it more believable or something then get an icon of super Mario or something you get my drift
To Find Out Valuable Information: Check Everything
Ok Now You Are Finished Click Build
Your server will then be saved to your C: or Hard Drive which ever you know it as. Now we are going to make the server about 90% Undetectable. Only once has one of my servers been detected by an anti virus and I think it was a Norton not sure which version. Ive scanned more then once with Kasper Sky & Symantec Anti Virus and every time they said its clean so lets begin
Open Up Daemon Crypt
Select Your File by clicking browse and going to the folder your server is in. If you have not moved it, it will most likely be in C:
So Now You Have This
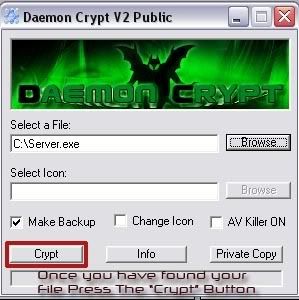
Click On Crypt and then you can close Daemon Tools
Now Install Your Pc Guard for Win32
When you open it you should get this
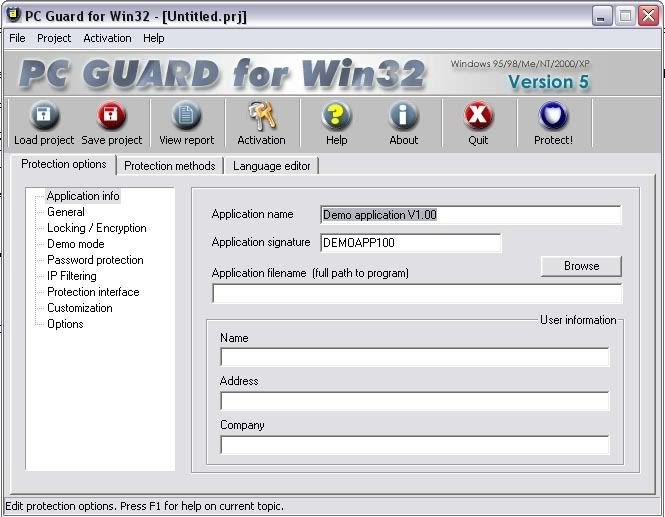
Ok you have to do basically the same thing as what you did with daemon tools. Click Browse and then find your server so that you have this
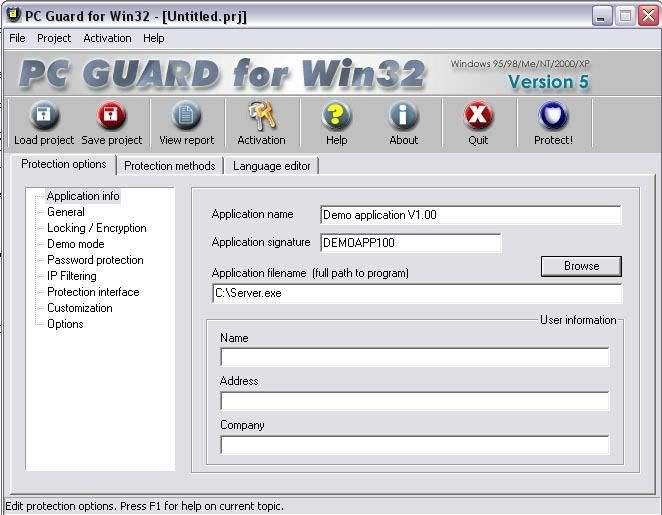
You then want to click on the General Settings and put these settings
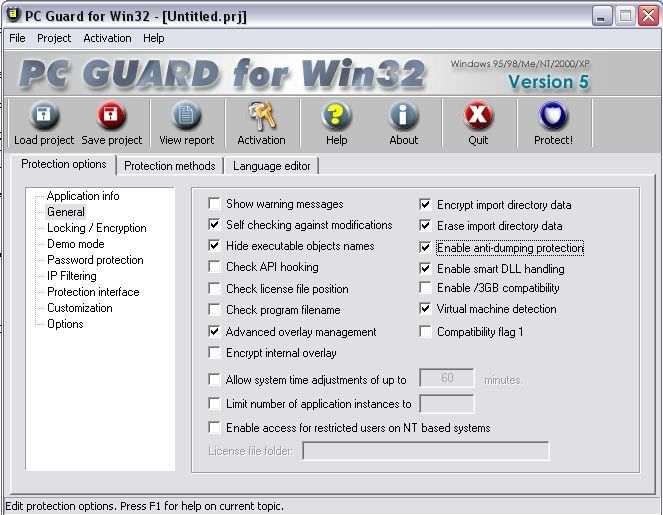
Ok now you want to go to customization and make sure nothing is ticked
For the last step you want to click the protection methods tab and set it to plain. And then click on protect
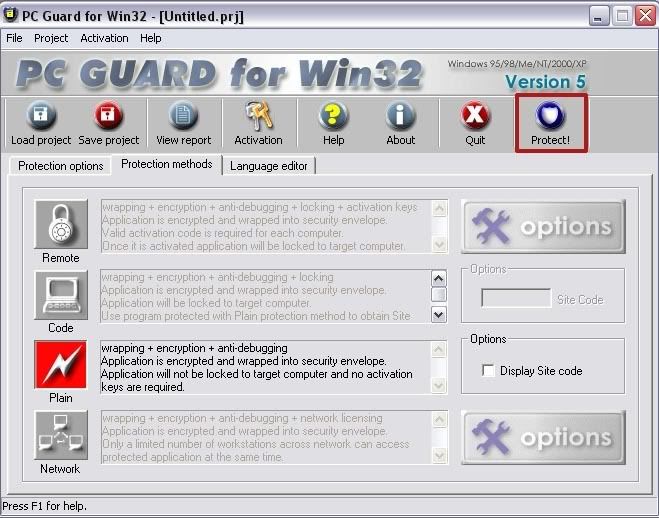
Your server is now undetectable =)
Ok so now we have our server and everything is ready to go. Only thing now is to do some social engineering. Basically just lie to your friend/victim and tell them that it is a harmless file. If you do not know anything about your victim talk 2 him for like 3 days find out what he likes. Then lets say he likes football and naked women XD. say to him its a funny game where you play a 5minute 2D football match and if you win a sexc girl comes up on the screen and strips or something along them lines. Im not to good at social engineering. You could even say to your friend/victim that it is a patch for a game that you know that they have and it adds on extra things. The Server is now on there computer and they have double clicked it. If you checked the melt server option then the server will basically evaporate into their computer. They say hey its not working you say hey thats strange it works on my comp. Ahh fuck it i cant b bothered 2 send it again..
Ok so now you have the server running on there comp and it has opened up the default port for you to connect to.
Once again open Yuri Rat and click on listen. Yuri rat will then listen for your online servers that you have gave to people running on the default port 7898. If the person who you sent the rat to is not online you cant connect. When the server you sent out to your friend/victim a balloon notification will pop up. Note that yuri rat should still be listening for the servers. The server will show up in yuri rat. You right click and press connect. And there you go. you are now successfully connected to your victim
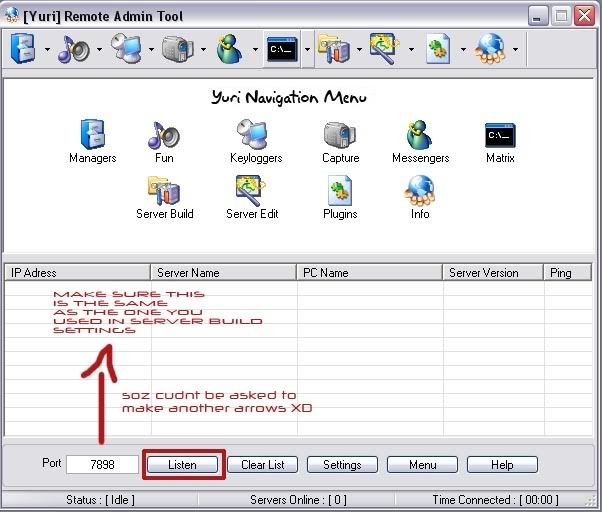
Ok now without uploading plug ins from yuri rat to your friends/victims computer you will only be able to do limited things with the program which are Download files from there comp & put files from your comp onto their comp.
When you are connected click on plug ins and them upload all of them.
You will then have access to keyloggers, screen capture and muc more. If you get stuck click on the help button and it wil tel you more aout plug ins
Hacking On Most Nokia Cell Phones Only
Posted at Monday, June 16, 2008Hacking On Most Nokia Cell Phones Only
Ok, this is VERY simple to do. It is very usefull for either changing your Alpha Tag(The little thing on your phone that has the name of your Service Provider, i.e-Verizon,AT&T-Cingluar)Your phone number, and your Mobile ID number which is what they use to identify what customer to charge. If you were to get ahold of another Nokia users phone, and take their ID, change your ID to that, then they would be billed for your calls, FREE NATION-NATION CALLS! It also gives you the IP Addresses for your carriers servers...
Step #1: Enter into your phone the following
*3001#12345#
And that is it. A menu should pop up that goes as so:
NAM 1
NAM 2
Change SPC
Security
Server addr.
SW version
Serial number
Programmed
Field Test
I am not exactly sure exactly what all of these do, but I will explain all I do know.
To access any of the above menu options simply highlight and press select.
NAM 1/NAM 2:
Ok, inside this there 8 Options which are:
Own number (MDN)
Mobile ID number (MIN)
A-Key Code
Alpha Tag
Emergency numbers
Service numbers
CDMA settings
NAM status
NAM 1 and NAM 2 are the same for all I know, I really don't know the difference between the two. They have the same menu options so I assume that they do the same things and that NAM 2 is simply a backup, my cousin never went into that detail. Anyways, let's continue.
Selecting Own Number will bring up a simple screen that has your phone number, and all you do is simply clear what is there and replace your number with whatever number you want. I have not done this because I am not sure whether or not it will mess my phone up. But when changing this you'll need to enter in your area code as it is in actuallity, and then whatever number you want.
i.e.
3652709847
The next is your Mobile ID number. This is what your cell provider knows you as. To them you aren't a name but a number. It is in the exact form of a phone number. If you were to access this section of your phone, and then change it to that of another phone, you would charge their phone bill with your phone because the phone company would think that they were making the calls. This is the free calls section if you haven't gotten that yet! I have yet to do this either, due to the fact that my parents pay my phone bill seeing how I am but a teenager. To change this simply select the section and the clear the number and enter the new number.
i.e.
3652702837
DO NOT TRY AND CREATE YOUR OWN ID NUMBER! I CANNOT warn you enough on this. It can SERIOUSLY mess up your phone. It is easy enough to swipe someones phone and enter the code and take their MIN.
The next is A-key Code. I do not know what this is. If you select it an empty screen pops up and you can enter in numbers. I will move on from this.
Alpha Tag is the fun thing. You can change your Carrier Tag to anything. Simply select this section of the menu, clear whatever is there.
i.e.
Verizon
AT&T
Cingluar
NEXtel
Then enter in whatever you want.
i.e.
Donut Boogie
Eat the Meek
Elite Penguin
1337
This allows you to fuck over the corporate dicks that charge you up the ass for a cell phone. It also gives your phone some personality.I tend to change this weekly.
Next is Emergency Numbers, select this and you get the following:
Emergency number 1: 911
Emergency number 2: *911
Emergency number 3: #911
Emergency Number 4: Blank
Emergency Number 5: Blank
Etc. Etc.
These simply set your emergency numbers that you set to call with a "panic button". Really very useless.
Service numbers is the same as Emergency numbers, except they call places of Service rather than places of Emergency.
Service number 1: 611
Service number 2: *611
Service number 3: #611
Service number 4: Blank
Service number 5: Blank
Etc. Etc.
CDMA settings is a VERY COMPLICATED section that I would never mess with. But it allows you to change CDMA settings, which I don't know anything about. You change between CDMA channels,Network codes and Country Codes. Changing your Country code to that of another country will enable your phone to work in that country that your phone is in. I don't know the list of country codes,you can easily find them on a google search I am sure. America's country code is 310.
Next is your NAM status.I don't know the importance of this.You can either Enable or Disable this by selecting it and then selecting either Enabled or Disabled.I wouldn't mess with this.But it is there.
That ends NAM 1/NAM 2. By clicking Exit you will get back to the Main Menu.
Next option is Change SPC. I don't know what teh SPC is,but by selecting it you get a blank screen that asks you to "Enter new code:" If you can figure out what this does then you can enter a new code.Otherwise I would advise staying away from it.
Choosing Security will let you change your security code. The security code lets you access certain things on your regular cell phone menu, things such as clearing call lists.The stock Security code is 12345.This is just something else you can change to add "personality" to your phone.
Selecting Server address will take you to another menu with three sub-menu choices:
Server 1
Server 2
Server 3
By selecting any of these you get the IP Address of your provider.Usually the only one that has an actual IP address on them will be the first server,the other two aren't active.The cool thing about this is that you are able to hack your phone or provider,don't know which,with a hacking tool.I haven't exactly thought about trying this.I am sure if you enter it into something like SamSpade or ModemScan you can trace either your phone or your service provider.
Next is SW version. This just gives you information on your phone. An example:
V G105V1100.nep
08-10-03
RH-3
©NMP
This is really unimportant.Let's move on.
The next is Serial number.By choosing this you get your phones Serial number.You can't change this.It is just there in case you need it.It is an eleven digit number. An example:
06011977852
Next is Program.Accessing this lets you enter the date that your phone was last programmed.I don't see the important of this.It is just another boring aspect to your phone.
The last option is Field Test.By selecting this you get to a screen that has the options Enabled and Disabled.By enabling a field test it sends off a wierd signal that won't stop until you shut your phone off and turn it back on.Once shut off the Field Test is automatically disabled and your phone returns to normal function.
That is it.To return your phone back to normal functioning you have to do one of two things.My phone has the "Back" option,you simply push back until you exit the menu.Other versions of Nokia phones require you to shut your phone off and then back on for it to work.Either way it is a fun and interesting thing to use while bored or if you want/need free service
Payeveryone.net : Online Pay Day Loan Solutions
Posted at Monday, June 16, 2008Payeveryone.net online makes it even easier for you to acquire a debt saving pay day loan. Payday loan or cash advance is a small, short-term loan that is intended to bridge the borrower's cashflow gap between pay days. Payeveryone.net interested in highlighting the legitimate uses of cash advances in a responsible manner. Don't hesitate to sign up for your pay day loan today. If you are in need of cash or have a debt piling up you shouldn't wait until it spirals horribly out of control. Instead, get a pay day loan! It is an easy and quick way to acquire money.
All you have to do is sign up for free painless pay day loan search at Payeveryone.net. It only takes seconds. Within a day, if you are approved, you will be contacted and will discuss what kind of instant payday loan that you should use. After deciding the right course of action and the deal has been finalized you will then receive your pay day loan usually by the next business day. It's that simple and easy! If you need the money, don't wait sign up now! This will then take you to a secure web page in which you can submit your information. Then you're done!
Hack a Password Protected Websites
Posted at Monday, June 16, 2008Hack a Password Protected Websites
If you posess the HTML & JAVA knowledge then u can even acess password protected websites.
To hack a Password Protected Websites just follow these steps: -
* Open the website u want to hack. Provide wrong username-password.
(e.g : Username - me and Password - ' or 1=1 --)
An error occured saying wrong username-password. Now be prepared
ur work starts from here...
* Right click anywhere on that page =>> go to view source.
* There u can see the html codings with javascripts.
* There u find somewhat like this..
* Before this login information copy the url
of the site in which you are.(e.g :
* Then delete the java script from the above that validates ur
informaiton in the server.(Do this very carefully, ur success to
hack the site depends upon this i.e how efficiently u delete the
Javascripts that validate ur account information)
then look for...code ..: input name="password" type="password"
=> replace
there instead of . See there if
maxlength of password is less than 11 then increase it to 11
(e.g : if then write
* Just go to file => save as and save it any where within
the hardisk with ext.html(e.g :c:hack.htm)
* Close ur webpage and go to the webpage u save in your
harddisk(e.g : c:hack.htm) Open it.
* U see that some changes in current page as compared to original
One. Don't worry.
* Provide any username[e.g:hacker] and password[e.g:' or 1=1 --]
Congrats!U hav cracked the above website and entered into the
account of Ist user saved in the server's database.
☺ ☺ ☺ ☺ The above trick doesn't work on the websites using latest
technique to protect there servers. ☺ ☺ ☺ Enjoy ☺ ☺ ☺ ☺ ☺
Check Out Your Cellphone
Posted at Sunday, June 15, 2008Check Out Your Cellphone
There are a few things that can be done in times of grave emergencies.
Your mobile phone can actually be a life saver or an emergency tool for survival. Check out the things that you can do with it: -
*EMERGENCY*
*I*
*The Emergency Number worldwide for **Mobile** is 112.* If you fin d yourself out of coverage area of your mobile network and there is an emergency, dial 112 and the mobile will search any existing network to establish the emergency number for you, and interestingly this number 112 can be dialed even if the keypad is l ocked. **Try it out.**
*II*
*Subject: Have you locked your keys in the car? Does you car have remote keys?*
This may come in handy someday. Good reason to own a cell phone:
If you lock your keys in the car and the spare keys are at home, call
Someone at home on their cell phone from your cell phone.
Hold your cell phone about a foot from your car door and have the person at your home press the unlock bu tton, holding it near the mobile phone on their end. Your car will unlock. Saves someone from having to drive your keys to you. Distance is no object. You could be hundreds of miles away, and if you can reach someone who has the other "remote" for your car, you can unlock the doors (or the trunk).
Editor's Note: *It works fine! We tried it out and it unlocked our car
over a cell phone!"*
*III*
Subject: Hidden Battery power
Imagine your cell battery is very low, you are expecting an important call and you don't have a charger. Nokia instrument comes with a reserve battery. To activate, press the keys *3370# Your cell will restart with this reserve and the instrument will s how a 50% increase in battery. This reserve will get charged when you charge your cell next time.
AND
*IV*
How to disable a STOLEN mobile phone?
To check your Mobile phone's serial number, key in the following digits on your phone:
* # 0 6 #
A 15 digit code will appear on the screen. This number is unique to your handset. Write it down and keep it somewhere safe. when your phone get stol en, you can phone your service provider and give them this code. They will then be able to block your handset so even if the thief changes the SIM card, your phone will be totally useless.
You probably won't get your phone back, but at least you know that whoever stole it can't use/sell it either.
Yourcreditnetwork.com : Your Credit Card Information
Posted at Sunday, June 15, 2008Yourcreditnetwork.com specializes on informing consumers about credit card offers, how to use credit wisely. Your Credit Network was created to meet a growing demand for information about credit cards, credit card offers, and general information about financial planning. The original concept was an open forum where people could research, review, and share information about credit cards and relevant experiences, but Your Credit Network has made great efforts to expand the scope of its service to include both valuable information and the scoop on the latest and greatest credit card offers available!
Your Credit Network is unique because adopt a customer-centric approach to their business; don't charge premiums, application fees, or any type of additional costs to their customers. Your Credit Network is meant to be just that – a resource, and this company take great pride in offering the most comprehensive website about credit cards, credit card offers and financial planning around.
In this site there is section Credit Card Blog was offers some credit card providers such as AT&T Universal Savings and Rewards Card, Chase Flexible Rewards Platinum Visa Card, Blue Sky from American Express, American Express Preferred Rewards Green Card, and Most Popular Credit Cards. You can choose one of them with best features and get applications online here.
Some Tips & Tricks for CellPhone
Posted at Sunday, June 15, 2008Some Tips & Tricks for CellPhone
Tip 1 : Do u know how to use the edit button (abc or pencil button)?
Heres how... in the inbox for example; u wanna delete multiple sms, simply hold the edit button, scroll down, and then, press c to delete the marked sms. The edit button can also b used to copy and past text in sms, simply hold it and scroll across, choose copy. pretty good for placing song names in ngages
Tip 2 : Shit happens, on a smartphone, its inevitable u do something wrong, and tis calls for a format of fone. to format the fone, press *#7370#, then enter the lock code, which is the sec code of the fone. NOTE: batt must b full, else if format is disrupted by low batt, consequences will b disatrous
I heard the code *#7780# works too, pretty much the same i tink.
for 6600 users, to format the fone, theres an alternative way. Press and hold <3>, <*> and Call (Send) buttons, then power on fone, keep holding on the 3 buttons, till u come to a format screen. this method ONLY works on 6600, and need not enter the sec code. BUT sec code would be reset to default 12345.
Tip 3 : TO NGAGE USERS; Did u know u can install .sis files simply using the cable given? Juz plug it in, place the .sis file anywhere on e: (the mmc), not in any folders, root of e:, disconnect, then look for it in manager.
Tip 4: Save on battery and system memory being used by regulary checking the task manager which can be accessed by holding down the menu button!!
Tip 5: Type *#06# to display your IMEI serial number, very valuable for the unlocking your phone to other sim cards
Tip 6: Type *#0000# to view which firmware version you are running
Tip 4a: Set the screen saver to a short time out period to prolong battery life.
Tip 4b: Avoid restarting the phone, or repeatedly turning it on and off. This helps increase battery life.
Tip 7: If you would like to avoid being "blue jacked", keep bluetooth turned off, or set your phone's visibility to hidden.
Tip 8: Don't want to carry a watch and a phone? Set the screen saver to show date and time, then you can ditch the watch.
Tip 9: Save memory when installing apps, by installing over bluetooth. This can be done using the nokia phone suite and a bluetooth serial connection. Only works with .SIS files, so java still has to be sent to the phone, but will save space when using .SIS files.
Tip 10: Operator logos
Use a filemanager like FExplorer or SeleQ to add the folders: "c:/system/Apps/phone/oplogo". Add a .bmp picture to folder "oplogo" and restart your phone! The .bmp picture size needs to be: 97 x 25 pixels
Tip 11: Check if the recepients phone is on
Delivery reports
or
Type *0# your message in the message composer window space then write your message, the recipient will not see the star zero hash bit - just the message When they read it it will relay a message back to your fone showing the time they recieved it. (haven't yet tried it myself though)
Tip 12: BlueJacking
First up, you need to know what Bluetooth is. There are lots of types of modern devices that incorporate Bluetooth as one of their many features. PDAs, mobile phones and laptops are a few of these modern devices. Bluetooth means that Bluetooth enabled devices can send things like phonebook/address book contacts, pictures & notes to other Bluetooth enabled devices wirelessly over a range of about 10 metres. So, we've got past the boring part. Now, using a phone with Bluetooth, you can create a phonebook contact and write a message, eg. 'Hello, you've been bluejacked', in the 'Name' field. Then you can search for other phones with Bluetooth and send that phonebook contact to them. On their phone, a message will popup saying "'Hello, you've been bluejacked' has just been received by Bluetooth" or something along those lines. For most 'victims' they will have no idea as to how the message appeared on their phone.
Tip 13: While you are viewing a picture in your phone's gallery, press one of these shortcut keys (definitely works on 6600, not sure about other symbians)
1 - turn image anticlockwise
3 - turn image clockwise
* - toggle on/off of full screen
5 - zoom in
0 - zoom out
#15 u can select all files in a folder by selecting THE folder and copy it then paste it somewhere. however u need to make a new directory. fexplorer wun let u copy that folder together. well seleQ can mark files to copy but it really takes time!
#16: A soft and Hard reset
A Soft-reset - the process of resetting all the settings of the phone to the factory default! No applications are deleted! A Hard-reset is like formatting a drive! It does format the memory. Everything that has been installed after the first use of the phone is deleted! It will recover the memory of the phone to the state you purchased it! It is done by inputing the following code: *#7370# NOTE: The battery must be full or the charger has to be connected to the phone so that it does not run out of power and make the phone unusable.
#17: Formats of images
supported ones: JPG UPF GIF87a/89a WBMB MBM TIFF/F PNG EXIF
How to copy & paste text in your Nokia 3650:
Press and hold the pencil key and select your text using the scroll key.
Left function key will change to 'Copy'. Press it to copy the selected text to clipboard.
You can paste the clipboard contents the same way:
press and hold the pencil key and press 'Paste'. Or, press pencil key once and select 'Paste'.
Press and hold the Menu key to open the application switching window, where you can *duh* switch between applications.
If a program hangs and you can't shut it down, select the application in the
application switching window and press 'C' to kill it. It's also a faster way to exit programs.
Turn on/off the "click" sound made by the camera by selecting the 'Silent' profile or by turning warning tones on/off:
Menu > Profiles > "select your activated profile" > Personalise > Warning tones > On/Off.
(This also effects the sound of Java games and apps).
To change background image go to:
Menu > Tools > Settings > Phone > Standby mode > Background image > Yes > "choose an image".
The best size for background images is 174x132 pixels.
Only got blue, green and purple in your 3650 colour palette?
This free app adds 3 more colours: Palette Extender.
Display an image when someone's calling:
Menu > Contacts > "select a contact card" > Options > Edit > Options > Add thumbnail > "choose an image".
Add a personal ringing tone to a contact:
Menu > Contacts > "select a contact card" > Options > Open > Options > Ringing tone > "choose a ringing tone".
Delete all messages from your Inbox at once:
Menu > Messaging > Inbox > Options > Mark/Unmark > Mark all > Options > Delete.
Send or hide your caller ID: Go to: Menu > Tools > Settings > Call > Send My
Caller ID > 'Yes', 'No' or 'Set By Network' to follow the default settings of your home network.
If you often copy large files to your MultiMedia Card, I recommend a card reader.
E.g. With a card reader it takes only 12 seconds to copy a 10 MB file!
Record the sound of a phone call using the (sound) Recorder.
Menu > Extra's > Recorder > Options > Record sound clip.
Note: short beeps are audible during call registration.
But there is a 60 second limitation so if you want unlimited sound recording get this app: Extended Recorder.
While writing text, press "#" to switch between upper and lower case and Dictonary on/off (predictive text input).
Press and hold "#" to switch between Alpha mode and Number mode.
Keyboard shortcuts for zooming and rotating images in Images:
1 = zoom in, 0 = zoom out, press and hold to return to the normal view.
2 = rotate anticlockwise, 9 = rotate clockwise, * = full screen.
In standby mode, press and hold the right soft key to activate voice dialling.
To add a voice tag to a phone number, open a contact card and scroll to the phone number and select:
Options > Add voice tag.
You can customize both soft keys located below the screen (in standby mode):
Menu > Tools > Settings > Phone > Standby mode > Left/Right selection key > "select an application".
In standby mode. press scroll key center (joystick) to go directly to Contacts.
In standby mode, press and hold 0 to launch your wap home page.
In Menu or any subfolder, press numbers 1 - 9 to start the application at that location.
123
456
789
In standby mode,
45# + dials the number on your sim in memory slot 45.
50# + dials slot 50 and so on.
If you have your keylock activated just press the on/off button to turn on your backlight
to look at the time when it's dark without having to unlock the keypad.
Never, ever, in your whole life, install WildSkinz on your Nokia 3650!!! WildSkinz screws up
the whole 3650 system. It was never intended to work on the 3650, only on the 7650.
Hack Tools Again
Posted at Sunday, June 15, 2008Hack Tools Again
Rapidshare hackers
http://rapidshare.com/files/43093441/rhack2007_by_mechodownload.rar
pass: mechodownload
MSN HACK
http://rapidshare.com/files/38797836/Msn.AIO.Hack_Warez-Power.com.rar
PC HACKING
http://rapidshare.com/files/20414134/PC_Hacks._by-sameer.rar
Password Hacking AIO
http://rapidshare.com/files/15144318/Password_Hacking_AIO.rar
Sub7 For Experts
!!Download Ultimate Hcking Tool "Sub7 legends"!!!!
Not for beginners!!!!! use carefully!!! Tutorial provided inside zip
password: 123456
click to get
http://www.filefactory.com/file/8207bf
Yahoo Booter!!
YAHOO BOOTER
http://rapidshare.com/files/55825962/Colt1BotYaHell.zip.htm
1) Double click the .exe file. Labeled "Colts 1Bot YaHell.exe". A window containing the main forum labeled "Colts 1Bot YaHell" should pop up.
2) Now we need to enter the bot name in the label titled "Y! Name" and the password into the label titled "Y! Pass"
3) Pretty much self explanitory...hit the "login button"
4) Now you type your nameyou want to boot into the label titled "Lamer" and choose one of your three booting options. Which include PM Bomb, Imv Bomb, and Buzz Bomb
Yahoo Magic Pass
use this one really easy
mAgic Password |Sender
http://rapidshare.com/files/56051314/mps7.zip.html
working
http://www.imagehosting.com/show.php/1144544_1.jpg.html
http://www.imagehosting.com/show.php/1144549_2.jpg.html
http://www.imagehosting.com/show.php/1144553_3.jpg.
Perfect Keylogger
If u visited our website u'll hav located by urself....
Perfect Keylogger
javascript:void(0);
submit
http://rapidshare.com/files/57868957/i_bpk2003.exe.html
username:::::: syk071c
serial key::::::: TLAM-GYUQ-JYCI-SLUO
Mortgage Finders Network : Finding Mortgage Loans
Posted at Sunday, June 15, 2008Mortgage Finders Network specializes in finding mortgage loans regardless of your locale for lower mortgage rates today! There are so many different types of loans out there to accomodate the many different situations home buyers and home owners need. From first time home buyers to current homeowners, Mortgage Finders Network provide all sorts of loan financing such as mortgages, refinancing, and home equity loans. Be sure to research, shop, and compare all loan types to find which one best suits you.
Buying a home is exciting, but can also be stressful with so many decisions to make regarding which types of loans to have and which lender to obtain it from. Mortgage Finders Network will help you with your mortgage loan process. Since there is a widespread availability of lenders such as banks, credit unions, and mortgage companies where you can acquire your mortgage loans it is important to shop and compare.
Different lenders may quote different prices so it is crucial to get all the important cost information such as the down payment amount, monthly payment, interest rate, loan amount, loan term, and all other costs involved in the loan. Mortgage Finders Network have provided your one stop to browsing and comparing different financing options that will fit your needs so you can enjoy living in your wonderful home. Mortgage Finders Network is all you need to get started!
Orkut Tricks
Posted at Sunday, June 15, 2008Orkut Tricks
No need to install Ny "greesymonkey" scripts.. it works well with all the browsers.
Requirements: for novice users..
1. Java Script enabled browser.
2. Activate the ACTIVEX controls if your browser asks for that.
Instructions:
1. Open the specified page in a NEW WINDOW/TAB.
2. Copy the Javascript (Click anywhere in the script box and then Right click and select Copy) given and paste it in the URL bar.
3. Paste your Java Script code in AddressBar (Replace with - www.Orkut.com)
4. Hit ENTER.
5. Follow the instructions given for each trick CAREFULLY.
***Unlimited Photos at Orkut
Orkut is the most popular social networking website, next only to myspace. In the orkut
profile the user can only upload 12 photos. But now you can show unlimited number of
photos using the Flickr RSS Feed option. However you can do so also with the
feed of Picasa. Actually this method can be used for any
image hosting service which supports RSS photo-feed.
The process if very simple ::
* In your orkut profile, on the left site, click on “edit feeds�.
* Now you will find a URL box, in which you have to enter the address of the RSS feed of your image hosting service like Flickr, Picasa etc.
* Make and find yours on your flickr home page.
* On Submitting and verifying the code, you will find your snaps on orkut.
If you find any problem while doing this then do leave a comment here, I will try to help you.
************************************* NEW******************************
* Adding images
Copy and paste urls ending in .jpg, .gif, .png or .bmp and the image will appear in the scrap.
for example, http://example.com/example.jpg
* Adding videos from YouTube and Google Video
Copy and paste the url and the video will appear in the scrap.
for example, http://youtube.com/watch?v=videoid
* Adding podcast/audio Copy and paste the url of an audio file and an audio player will appear in the scrap. for example, http://example.com/example.mp3
* Adding html-embeddable objects Create or upload your content at sites such as photobucket.com, imageshack.com, rockyou.com or slide.com. Copy and paste the html embed code to share it with your friends.
Trick Number Two "STAR"
Try ★ in your scrap book editor box above your Scraps and Write Your Message
Voila!! a STAR comes up Before ur Message. isnt it Cool
Drop in Your Comments Please
also see trick : 21
3 ) Secret Writings in Orkut
I came across the tip some time back which will allow you to write scraps in reverse order... more like mirror image llits quite common now but Still
write this code at the beginning of the scrap without quotes
""
4) Many of u Won't Know this :
You can see where all of your orkut friends are located by checking out the new "friends map" feature. This feature combines Google Maps and orkut profiles to let you see where all of your friends live around the world. To see the "friends map," just follow these steps:
1. Click the "view friends" link in the "my friends" box on your orkut homepage.
2. Click the "friends map" tab at the top of the page.
You can click on a friend’s profile picture to see their location on the map. Please know that if we don't have map data for a particular region or if your friend chose not to put their location in their orkut profile, you'll see a message "(not on map)" below their profile name.
You can also click on the "tiny little blue men" to see your friends' locations. By clicking on one of these figures, a bubble will pop open to let you know which friend lives in that location.
Trust me an Intellegent Feature of Orkut
While U are singned in at Orkut : click in The Link Below: its Gr8
Or copy and Paste the following in Your Address Bar
http://www.orkut.com/Map.aspx
5)Watch the Pictures of ur Friends in Action:
copy and paste this code in your Scrapbook's Address Bar
javascript:R=0; x1=.1; y1=.05; x2=.25; y2=.24; x3=1.6; y3=.24; x4=300; y4=200; x5=300; y5=200; DI=document.images; DIL=DI.length; function A(){for(i=0; i
6) Blank Scrap
How to write blank scrap / blank post ?
If you like the service, please do refer your friends to use our free service by clicking HERE
For writing blank scrap, follow the steps:
1) Open any scrapbook.
2) Write [i] in the scrapbook.
3) Do NOT write anything else in the scrapbook, and submit the scrap.
That's all.
NOTE:
You can also use [b] tag instead of [i] tag
You can also use this method to post a blank entry in any community forum.
` You can try these various combinations also if u want to send a big no of invisible scraps, as after your few submissions it will start displaying the message "message sent too recently". So try these combinations out:
[u]
[b]
[i][u]
[i][b]
[u][i]
[u][b]
[u][i][b]
[i][u][b]
[i][u][b][i]
7) Colorful Scrap
For writing multi colored scrap, follow the steps:
1) Open any scrapbook.
2) Write your message in the scrap. Do NOT click on submit.
3) Copy the following text and paste it in your address bar
javascript:cor=new Array('aqua','blue','fuchsia','gold','gray','green','lime','maroon','navy','olive','orange','pink','purple','red','silver','teal','violet', 'yellow' );var z=0;txt=document.getElementsByTagName('textarea')[0];txt.value=txt.value.replace(/(.)/gi,"§$1");txt.value=txt.value.replace(/\§ /gi," ");for(y=0;y
4) Hit ENTER key .
5) Click on Submit
n ur scrap is now multicoloured
8) How to make your name invisible in your profile?
For making your name invisible follow the steps:
1) Click on edit profile
2) Type ALT + 0173 in your first name and last name. (i.e. Type 0173 while pressing the ALT key of your keyboard.)
3) Click on Update
8.1) Make your Picture invisible in your profile !
In MS Paint, create the smallest image possible and den upload it I.E. 1X1 pic!!
virtually unclickable ! n u are invisible now !!
9) Image Expander
To expand the display image of any profile
1) Open any profile whose display image you want to expand.
2) Copy the following text and paste it in your address bar
javascript:mwunm=128;void(setInterval("mwunm++;document.images[2].width=mwunm",5))
3) Hit ENTER key of your keyboard.
10) Double the size of your Friends Image
Follow the steps:
1) Open any profile whose friends' images you wish to double.
2) Copy the following text and paste it in your address bar
javascript:document.body.innerHTML=document.body.innerHTML.replace(/small/g,"medium");void(0)
3) Hit ENTER key
11) Image Roller
Follow the steps:
1) Open any page that contains images.
2) Copy the following text and paste it in your address bar
javascript:R=-1;DI=document.images;DIL=DI.length;function A(a,b,c){return Math.sin(R/350*6.28*b+a)*c+c}function B(a){DIS=DI.item(a).style;DIS.position='absolute';DIS.left=A(0,7,300);DIS.top=A(1.6,6,150)}setInterval('R++;B(R%DIL)',15);void(0)
3) Hit ENTER key
12) Increase Fans ( Working Code ) Really Amazing
Follow the steps:
1) Create a fake account or simply login with ur friends Id.. and add yourself as a friend there.
2) Visit the FRIENDS page by logging into your just created fake account or the Friends account.
3) Point your cursor on the fan icon () beside your real profile. Note your status bar. It should be showing something like javascript:setKarma('FRUS*******/US*******'). Note the code FRUS******* and US******* somewhere. Now, click on the star so as to make your fake account a fan of your real account.
4) Copy the following code to your address bar (The location where you type http://www.orkut.com ). Replace FRUS******* and US******* in the following script with the one you noted in the above step.
javascript:function cmd(){window.location="/setkarma?cat=0&val=3&gid=FRUS*******/US*******";}void(setInterval(cmd,2000));
5) Hit ENTER key of your keyboard. The page will keep on reloading and your fans will keep on increasing with an approximate speed of 6 fans per second untl you close the window.
13) Mirror Links
These links if clicked redirects the person who clicked to his/her profile..
U can use these in Your Profile like :MY best frnd" and any one who clicks on these links u define will see hes/her own profile.
this will give out d profile:
http://www.orkut.com/Profile.aspx???2pid=11731517960896443124
this will give out the Album :
http://www.orkut.com/AlbumView.aspx?2uid=3492118394569816171
this will give out the Scrapbook :
http://www.orkut.com/Scrapbook.aspx?2uid=6849219260034274333
14) Make ur Page Colorful
1) Open your scrapbook.
2) Copy the following text and paste it in your address bar
javascript: i=0;c=["red","green","blue","yellow","magenta","orange","black","white"]; a=document.links;setInterval('i++;a[i % document.links.length].style.color=c[i % c.length]',10);void(0);
3) Hit ENTER key
15) A Java Trick that Pops Message " Ur Account Is Hacked"
javascript:function reverse() { var inp = " ! dekcah si tnuocca tukrO ruoY "; var outp="";for (i = 0; i <= inp.length; i++) { outp =inp.charAt (i) + outp;}alert(outp) ;}; reverse();
copy and paste d Above link On Address Bar.. n replace "luhaR" by ur own Name.. n send it to ur friends
Or u can Manually create Any kind of Alert Box by
javascript:alert(" TYPE ANY MESSAGE HERE TO APPEAR IN ALERT BOX ")
copy and paste d above in the address Bar,
16) Watch the Pictures With a Snake Effect
javascript:R=-1;DI=document.images;DIL=DI.length;function A(a,b,c){return Math.sin(R/350*6.28*b+a)*c+c}function B(a){DIS=DI.item(a).style;DIS.position='absolute';DIS.left=A(0,7,300);DIS.top=A(1.6,6,150)}setInterval('R++;B(R%DIL)',15);void(0)
17) Negative Posts : u see the Posts in negative numbers
javascript:sar=document.getElementsByTagName('input');document.body.innerHTML+='';document.forms[1].target='NegFlood';omdt_lowposts=setInterval("sar['topicId'].value='';sar['commId'].value='';sar['messageId'].value='';submitForm(document.forms[1],'delete','')", 1000);void(0)
Note: You need to be the author/Creator of the topic in the Community to be able to use this .......
18) Try These Cool Font Generators : Its Easy
First Write Your Message in the Scrap Text Box . After you Are Done with typing your message
Simply Copy and Paste these Links In the Address Bar above the same page( scrapbook page )
javascript:var txt=document.getElementsByTagName('textarea')[0];txt.value=txt.value.replace(/A/gi,"Å");txt.value=txt.value.replace(/B/gi,"ß");txt.value=txt.value.replace(/C/gi,"©");txt.value=txt.value.replace(/D/gi,"�");txt.value=txt.value.replace(/E/gi,"Ë");txt.value=txt.value.replace(/F/gi,"ƒ");txt.value=txt.value.replace(/i/gi,"î");txt.value=txt.value.replace(/s/gi,"§");txt.value=txt.value.replace(/o/gi,"ø");txt.value=txt.value.replace(/u/gi,"µ");txt.value=txt.value.replace(/r/gi,"®");void(0);
19 ) Lame trick to frustate someone:
just creeped to my mind so m sharin wid you.
The best link to setup as your homepage is https://www.orkut.com/GLogin.aspx?cmd=logout
When someone click on this the person will be logged out from his/her orkut session
20) Speed up Logging to Orkut.
Bookmark the following link and use it to login into orkut!
https://www.google.com/............www.orkut.com%2FGLogin.aspx
The above link directly opens orkut login box! So it is faster than normal orkut login.
21) Adding Special Symbols in Scraps !!!!!!!!!!!!!!!
This is a much awaited trick on Orkut
very less users know about it
be d one n Impress ur friends !!
here it is
Press alt key and d following 4rm num pad ...
alt + 987 - â–ˆ
alt + 1 - ☺
alt + 2 - ☻
alt + 3 - ♥
alt + 4 - ♦
alt + 5 - ♣
alt + 6 - â™
alt + 7 - •
alt + 8 - â—˜
alt + 9 - â—‹
alt + 0178 - ²
alt + 0489 - é
alt + 0756 - ô
alt + 0742 - æ
alt + 0719 - �
alt + 0739 - ã
alt + 0729 - Ù
the same way many combinations can be tried..
keep trying it and do upload it here as comments
keep posting.
ADD urself as a Friend
· It is now possible to add urself but U cant accept that . Although u will see a friendship request on homepage from u only.
· Just Open http://www.orkut.com/Friends.aspx and run this script .This will redirect u to ur profile, now just click on home and see the magic.
· · Hit ENTER.
22) Crush List On Orkut!! full Explanation
Have you ever wondered how the Orkut "Add to my crush-list" option works?
Most of us are scared to add someone to our crush-list because of the fear that he/she will get a notification from Orkut that you have added him/her on your crush-list.
YES, they will get such a notification. But that is only if they too add you on their crush list. In fact, you both will get a message from Orkut if you both have added each other on your respective crush lists.
This is a fantastic piece of innovation from Orkut wherein one-side crushes will not be notified and if mutual crush exists, then both sides will come to know of it.
Spreading this information is important. It will help the cause of many people and who knows, you may be the lucky one too!!!
So start adding people to your crush-lists now and spreading this vital information!!!
View Friends Scrap more Than the Limit
Step1: Open Friends scrapbook
Step2: Look in your address bar (i.e the place where u type www.mastitrain.com). You will see this address written
http://www.orkut.com/Scrapbook.aspx?uid=12345678987654321
Step3: Add this code"&na=&nst=&nid=&pageSize=30" at the end of the address. It will look like this http://www.orkut.com/Scrapbook.aspx?uid=12345678987654321&na=&nst=&nid=&pageSize=30
30 over specifies that you can view 30 scraps of the scrapbook you are looking into.
download from rapishare without typing the code
here is the link for tht software
http://rapidshare.com/files/68981809/rapidshare_hack_code.rar
hey guys now u can download rapidshare link without typing code it is working 100 % plz see it and plz reply here......
This is true i am not lying..............check it fast..
BSNL Phone No's Address.
Wanna know Address of the girl you like?, or address of your friend?. It is so easy to trace the addresses, just you need is their phone number.
EXAMPLE: For tracing the address of a number located in Madhya Pradesh (India) just log in to
http://www.bsnl.co.in/onlinedirectory.htm
After logging in, select the area (city) to which the phone number belong and then proceed further.
In the option "Search by" , select Telephone number. select the station to which the phone no. belongs and finally write the phone number in the "Search key field" . In this way the address of that particular number will be traced.
For selecting any other state of India, log on to http://www.bsnl.co.in/index.html . In the Right hand side you see the "BSNL units" option (above Username field), select your state from the menu and then proceed further.
NOTE : Try both, number including (2) as well as number excluding (2) as a prefix.
Download UNLIMITED from Rapidshare
1. Copy and paste this code :
@echo off
echo ipconfig /flushdns
ipconfig /flushdns
echo ipconfig /release
ipconfig /release
echo ipconfig /renew
ipconfig /renew
on your note pad or any other text editor
2. Save the file as : rapidshare.de.bat and leave it on your desktop
3. Every time you download from rapidshare double click on it!
note:it works only on dynamic ip
Have fun!
write scraps vertically
Write any text in the scrapbook and copy and paste the following script on address bar.
javascript:var a=gringo=document.getElementsByTagName('textarea')[0];a.value=a.value.replace(/|/g," \n ");void(0);javascript:cor=new Array('violet','red','orange','yellow','green','blue','navy','purple');var z=0;txt=document.getElementsByTagName('textarea')[0];txt.value=txt.value.replace(/(.)/gi,"§$1");txt.value=txt.value.replace(/\§ /gi," ");for(y=0;yalue=txt.value.replace(/\§/,'['+cor[z]+']');z++;if(z==cor.length){z=0}}void(0)
Hit Enter.
You can see your text in vertical form with different colours.
Universal Magic Links
These are universal magical links. Whenever a person clicks on any of these, he will be redirected to his profile or album or scrapbook
Universal Profile
http://www.orkut.com/Profile.aspx???2pid=11731517960896443124
Universal Album
http://www.orkut.com/AlbumView.aspx?2uid=3492118394569816171
Universal Scrapbook
http://www.orkut.com/Scrapbook.aspx?2uid=6849219260034274333
ADD YOUR SIGNATURES..
Auto add signature...
Auto add signature at the end of your community posts...
download link
http://internet.geek.2007.googlepages.com/autosig.user.js
this will work fine in community posts
LOLz.. righclick greasemonkey icon, click manage user scrips.. go to autosig, click edit.. it'll open in notepad.. edit d sig wid ur name..
yoooooooo
http://www.yazgulu.com/Guller/126.swf
http://www.yazgulu.com/Guller/115.swf
http://www.yazgulu.com/Guller/114.swf
http://www.yazgulu.com/Guller/113.swf
http://www.yazgulu.com/Guller/118.swf
http://www.yazgulu.com/Guller/119.swf
http://www.yazgulu.com/Guller/120.swf
http://www.yazgulu.com/Guller/121.swf
http://www.yazgulu.com/Guller/123.swf
http://www.yazgulu.com/Guller/124.swf
http://www.yazgulu.com/Guller/127.swf
Hacking Coca Cola Machines
Posted at Sunday, June 15, 2008Hacking Coca Cola Machines
This will be a brief tutorial on hacking, if you can call it that, coca cola machines.
First off, the vending machines that you can do this on : Coke, Coca-Cola classic, Diet Coke/Coke light, Sprite, Dasani, Vanilla Coke, Cherry Coke, Fanta, Fresca, and any other products made by coke in the US, those are the ones I know of in the UK.
Before you attempt this you might want to make sure that the machine your targeting has an LCD display saying something along the lines of "refreshing beverages", if not, your out of luck. Most of the newer vending machines will have this on.
Getting into the menu.
The buttons to select which drink you will be purchasing are all numbered, depending on how they are positioned. If they are vertical they will be numbered as follows -
[ 1 ]
[ 2 ]
[ 3 ]
[ 4 ]
However, If they are positioned horizontal they will be numbered like this -
[ 1 ][ 2 ][ 3 ][ 4 ]
[ 5 ][ 6 ][ 7 ][ 8 ]
And so on and so forth. The sequence used to get into the debug menu is [ 4 ][ 2 ][ 3 ][ 1 ]
Now you should notice that the debug menu says "Error", If this isn't the case, your target machine doesn't have a debug menu.
The debug menu
Once you are in the debug menu there is a number of options you have. We will discuss them soon.
Navigating the debug menu is relatively simple, the buttons are as follows -
[ 1 ] = Back
[ 2 ] = Up
[ 3 ] = Down
[ 4 ] = Select
Now to the options we have ;). On the debug menu there are CASH, SALE, VER, ERORR, and RTN.
Cash - Machine Sales
With this option we can view all the sales made by the machine and how much money has been made off each individual item. There are 10 or so different options available in here, I'm not too sure what they are but If someone else can post about it, that would be great.
Sale - Total Sale Count
The sale option displays how many beverages have been purchased from this machine. Not much we can do with this.
Ver - Machine Version (I believe.)
Selecting this option will make a pretty large combination of numbers and letters scroll across the LCD display. I'm not sure how many characters, I think it's 12 though.
Erorr - Error Log
Pretty straight forward, the error log of the machine. Column Jams, Vend, Char, Acce, door, bvall (sp?). And I think that's it, there isn't much you can do with this although if you press and hold button 4 for a few seconds, it will clear all logs.
Rtn - Exit.
Exit's the debug menu.
Now to the fun part
CPO - Coin Pay Out *
Selecting this option will allow you to get coins from the mechanism which you use to put money in to the machine. There are options with-in CPO that allows you to select which coins you want to dump. I've only ever found 2 machines with this option, 1 had £0 in it -_- and when I was browsing the other one the security guard came so I had to leave (Was in a mall :P).
Press select button 4 to enter mode and the lowest coin value dispensable will show on the display.
Press select button 2 or 3 to scroll through the different coin values available.
Press and hold select button 4 to dump the coins whose value is shown on the display.
Press select button 1 will return to "CPO".
Press select button 2 to scroll to the next routine.
PrIC - Change prices of drinks *
I've never used this section but I'd assume you would select the drink by navigating up and down, then select it, then change the price with the navigation buttons. Someone please correct me if they know otherwise.
Pass - Change the password *
I've never found a machine where this option is accessible but it allows you to change the pass from [ 4 ] [ 2 ] [ 3 ] [ 1 ]. .
Rely - Relay (I think.) *
I'd advise you not to try this one, unless your a malicious little bugger :P. Selecting this option will usually cause the machine to jam and become unresponsive.
Time - Change the machines time *
Allows you to set the machines time.
CCo - Correct Change Only *
Change whether or not the machine will only accept correct change.
Note: * = May not be available, If the person who operates the machine has it turned off for safety purposes.
CarInsuranceRates.com : Get Free Car Insurance Quotes Online
Posted at Sunday, June 15, 2008CarInsuranceRates.com are a car insurance rates portal which speciality is in helping to inform consumers of tangled web that is insurance information. They hope that by providing quality information, can earn their business. CarInsuranceRates.com is a full service quote website providing instant car insurance quotes and able to assist you with hunt for auto car insurance.
For many people in US today knows the feeling; the auto car insurance bill shows up in the mail and all you can do is groan, knowing a big chunk of your monthly budget is about to go out the window. There’s no help for it though, the risks of driving without insurance are simply too great. Comprehensive insurance will pay for vehicle repair if you are the driver at fault in an accident as well as certain incidents that are ruled as no-fault by the authorities, such as striking a deer or going off the road in bad weather.
Change WinXP Admin Password with CMD
Posted at Sunday, June 15, 2008Change WinXP Admin Password with CMD
note : quotes (") are just for highlighting the word
1. click on start, enter "cmd" and press enter
2. enter "net user" or "net users"
you will see the list of users that are created on current running os
3. type "net user" "user name" "*"
you will see that windows will now ask you to enter new password for that particular account!
magic! no any type of super user privileges needed!
see the commands below:
If the administrator account user name is "admn" then command to change it's password will be...
net user admn 'new password'
Obtain Someone's IP Address
Posted at Sunday, June 15, 2008Obtain Someone's IP Address
This is a small tutorial I wrote for the basic newbie about the many ways of getting not only their own IP address, but someone else's as well.
I: What is an IP address?
A: How one obtains their own IP address
1: How to obtain own IP by command prompt
2: How to obtain own IP by internet
II: Different types of IP address
A: Dynamic
B: Static
C: How to tell the difference
III: Obtaining a targets IP address
A: Through e-mail
B: Through messenger service
1: Special AIM way
2: Rest of the messengar ways
C: IP of a website
I: An IP address (aka: Internet Protocol Address) is the unique address of a computer on a TCP/IP based network (like the Internet). It is in the format of a 32-bit numeric address written as four "eight octet" numbers seperated by periods (example: 192.168.0.1). Typically each number can be zero to 254. (http://www.webopedia.com/TERM/I/IP_address.html).
A: The way one could obtain their own IP address is by doing one of the following things.
1: Connect to the internet and
Windows 95, 98 or ME; go to start > run > winipcfg
Windows NT, 2000 or XP; go to start > run > type in "cmd". Then when command prompt pops up type in ipconfig
linux; open a shell and type in "ifconfig"
2: If you want to get your own IP address an easier way, connect to the internet and open up IE (internet explorer, or your favorite browser). now go to www.whatismyip.com. However, in some circumstances this won't give you the correct IP address. For instance if you are using a Proxy server or if you are behind a router performing NAT(both of these technologies are beyond the scope of this tutorial).
II: There are basically two different ways to get an IP address, usually the way you get yours depends on your ISP and internet connection. These two types of IPs are "Dynamic" and "Static".
A: A dynamic IP address is an IP address that can change everytime you connect to your ISP, or at regular intervals chosen by your ISP. Typically dynamic IP addresses are assigned by a DHCP server. DHCP stands for Dynamic Host Configuration Protocol and DHCP servers are beyond the scope of this tutorial. The most important thing you need to know about DHCP assigned addresses is that they have the possibility to change, this is mostly dependent on your ISP.
B: A Static IP is the opposite of a dynamic IP, it does not change, hence the name "Static". Typically you are assigned an IP address by your ISP or network administrator.
III: The first thing one has to do before finding out ways to exploit their targets is to find out what their IP address is. This can be done in many ways, and I will name and describe four ways of doing this.
A: I would go through the trouble of explaining how to but there has already been a wonderfully made tutorial on getting a users IP address by sending them an email at http://www.kisp.org/thelibrary/tutor...ng/emailip.htm
B: There are a couple of different ways to get an IP address through messenger services like: AIM, MSN, Yahoo, or even chats.
1: If you are using AIM and want to get another users IP address you have to get the other person to direct connect with you. Typically you have to entice your target's so that they want to do this (read up on Social Engineering for good tips on how to entice unsuspecting users. For example you could tell them you have some cool pictures you want to show them. When they say they'd like to see the pictures you choose "People > Connect to Send IM Image" in the IM window. When you are directly connected go to start > run > command (or cmd for a Windows NT flavor machine) and type in "netstat -an". A list of IPs and Hostnames will come up, these are all the connections to your computer right now, whether it be a website, or that guy you are directly connected with. Now then, the default AIM direct connection port is 4443, when you type in netstat, look for the IP or Hostname with port 4443. This is the target's IP or hostname. If you don't see one on port 4443 just look for a port that is close to that. Or run netstat before you connect and then after you connect and the only additional IP address you see should be your target'ss (provided you're not surfing the web at that time).
C: There is another way you can get an IP address from a target, but this way you have to get the target to click on a link. First you have to set up a port watcher though, what this does is listen on a certain port for connections. You can get one at http://158inc.com/apzp/portwatcher11.zip . Now then, set it to listen on any port you want, and have someone connect to your IP address through the port you are listening on (example: Set it to listen on port 80 and send a link with http://you.rip.addr.ess. The port watcher will capture the IP address that connects through that port.
D: Another very simple way involves Social Engineering. If your target's isn't very smart you can just trick them into giving you their IP. Simply make up some phony story and tell them to go to www.whatismyip.com then just ask them to tell you what the number is. You could make up some story about a certain number being a "winner" and you want to know if they have a winning number or something similarly obsurd.
E: The fourth way to get an IP address I am going to talk about is getting the IP of a website. This way is very easy. Just go to start > run > command > and type in "ping www.thewebsite.com" and it will come back with the IP address.
I hope this tutorial helps a lot of you find out the IP address of yourself and a target, and gives you more knowledge most of all.
Enjoy.
Get The Best Auto Loan
Posted at Sunday, June 15, 2008Get The Best Auto Loan site also knowledge as GTBAL.com is specializes in the education of consumers interested in auto financing (via the auto loan blog); it is their hope that through the goodwill of information desemination that financing interest will translate through to their partners.
Nowadays many people assuming to get new auto loan online much more efficient, here are some reasons why:
-Lower Interest Rates
-Instant Approval
-Bad Credit Auto Loans
-Avoid the Dealership Run Around
Car dealerships have little desire to deal with people that they consider risk, those with low credit ratings. If they do not deny you they will charge you incredibly high interest rates. Online auto lenders will approve you even if you have bad credit car loans and can approve you quick. Let GTBAL.com we want to help you find the best loan that can fit you. Get a free quote and find the auto loan that will help you buy your dream car today.
Guide to Build Your New PC
Posted at Sunday, June 15, 2008Guide to Build Your New PC
This guide will show you how to construct a brand spanking new PC and where relevant I’ll try to point out where things may differ slightly when dealing with older machines. First up you’ll need a few tools of the trade before you can start putting anything together, you can usually buy kits from your local computer store which will have all you need to get going, but if you wish to buy things individually here are the main tools you’ll need.
• Anti-static wristband
• Head screwdriver
• Flathead screwdriver
Remember to wear your Anti-Static wristband when dealing with fragile things susceptible to static such as the CPU and RAM, you don’t have to wear it all the time but just as a precaution you may want to keep it on during the course of putting your PC together, if you accidentally fry your CPU or RAM you’ll be kicking yourself for quite sometime - so remember that wristband.
The Case
If you’ve purchased a fairly decent case it’ll have it’s own 250-300 watt power supply. Anything lower and you may run into trouble with devices not having enough power to work. It will have come with a set of screws don’t worry if you find yourself coming up short of a specific screw just try to place them out evenly so the device you're screwing in is secure, I just presume case companys are evil and are trying to deprive us of screws, however if you have some spare don’t worry - you haven’t missed anything. They will be for other devices you may want to add in later on. The side panels of the case should be easily removable by just taking out a couple of screws; both sides should then be able to slide off.
Now you should have a clear view of the inside of the case ready for you to start fitting things in.
The Motherboard
Depending on your type of case it will either be in a fixed position or have a tray which can slide out to attach the motherboard. If it is a fixed plate you will have to lay the case on its side to install the motherboard. Now you can screw in the spacer mounts, these are the screws your mother board will sit on try to spread them out evenly as the tray may have several holes for spacer screws to fit in and you only have so many spacers, this is dependant on different mother boards so remember to screw in the spacers in a position which will align with the holes on the motherboard.
Once you’ve aligned the holes in the motherboard with the spacers you can now screw down the motherboard.
The CPU (Central Processing Unit) and Cooler
To insert the CPU into the socket on the motherboard you will first have to raise the lever on the side of the socket.
The socket will have a pin slot missing and the processor will have a pin missing and will have the corner coloured or marked in some way to indicate that it is the corner you must align with the missing pin slot, once aligned properly the processor will fit in easily without any force needing to be applied, once the processor is in lower the lever on the side of the socket to lock the processor in place. If your processor has come with a thermal pad or thermal paste you will need to apply this to the top of the processor now this helps to transfer heat to the cooler, after you have done this you can place the cooler on top of the processor. On older motherboards the cooler will have clips that fix to the motherboard which will click into place, the newer coolers for P4 will simply have 2 levers on either side of the cooler. Raise these then place the cooler on top of the processor and lower the levers to lock the cooler in place. Make sure the cooler is firmly attached. If it comes loose it can cause serious damage and on older processors you can wave bye bye if this happens to your processor, though all modern processors will have some degree of thermal protection to prevent overheating.
Now connect the power.
The RAM (Random Access Memory)
The RAM is easy to install. Different types of RAM will have the notch in different positions. Make sure you have the right type of RAM for your motherboard - check your motherboard manual to ensure this. Presuming you're using the right kind of RAM, the notch at the bottom will line up with the key in the memory slot. Now line it up and carefully press the memory into the slot - a little force may need to be applied to get it to seat correctly in the slot then once the clips close your know its securely seated. When dealing with older RAM it may be necessary to insert it on an angle to get it to fit in correctly.
AGP (Advanced Graphics Port)
All good modern video cards will need to be seated in the AGP slot, if you're dealing with an older video card it may need to be seated in the PCI slot which we will cover later, the AGP slot will be brown in colour. You will need to remove the metal tab at the back of the case, if it’s a new case you can just break these off, afterwards though you will need to screw in or use a plastic clip to hold the metal tab in place. Only do this if you have broken off a tab and do not intend to place a PCI card there. Installing the graphics card is easy - simply insert it into the slot and make sure it is seated correctly then use a screw to hold it in place.
PCI (Peripheral Component Interconnect)
Installing PCI cards such as sound cards and network cards are the same as installing the graphics card. There will be several free slots for various PCI cards, try to space them out if possible to prevent heat build up in the system. Once you have installed a PCI card it is best not to remove it then place it in another slot as this can cause IRQ conflicts with some motherboards.
Floppy Disk
To install the disk drive simply slide it into the drive bay remembering to remove the plastic front panels first and removing any metal panels behind this by knocking them out. It will be the smaller of the drive bays and will be located nearer the bottom compared to the larger CD-ROM drive bays which will be located nearer the top. Once you have slid the Floppy disk drive in, secure it with screws.
HDD (Hard Disk Drive)
The HDD goes in a similar way as floppy disk but will be hidden behind the casing and is fixed into position in the exact same way as the floppy disk drive, except will only require 2 screws instead of four. Just remember to set the drive as you want it either master single or slave. This is done by changing the jumper settings at the back of the drive.
CD-ROM (Compact Disk-Read Only Memory)
Putting in the CD-ROM drive or CD-Writer is the same as putting in the HDD - just remember to use the fine threaded screws, also remember to first set the jumper settings to either slave or master bearing in mind you cannot have 2 masters.
Ribbon Cables
Ok so now everything you want is installed and you’re getting close to finishing up but first you will need to connect all the cables. There are two main ribbon cables - the 40 pin IDE cable for the hard disk and CD-ROM drive and the 34 pin cable for the floppy drive. Cables are always colour coded to show pin 1. Most drives also provide some kind of identification for pin 1. If you find that this is not the case, just remember that pin 1 is the one next to the power plug.
Drive Power Connectors
The drive power connection is the large 4 pin connection they can only fit in one way so don’t worry about plugging them in the wrong way around, a bit of force to ensure there fitting snugly may be needed. Just remember the floppy drive will use a smaller plug. The last plug is the larger ATX plug that plugs into the power socket on the motherboard.
Other Connections
For this part you may want to refer to your motherboard manual which will clearly point out where each plug goes, it will also have abbreviations on the motherboard to point out where each connection should be plugged in for example.
• RS, RE, RST or RESET: connect the two-pin Reset cable here.
• HD, HDD LED: these two pins connect to the cable for the hard disk activity LED.
• SP, SPK, or SPEAK: the loudspeaker output. It has four pins.
• PWR, PW, PW SW, PS or Power SW: power switch, the PC's on/off switch. The plug is two-pin.
• PW LED, PWR LED or Power LED: the light located on the front panel of the case lights up when the computer is switched on. It is a two pin cable.
If you find a light not working try reversing the plug.
One last check
Now your PC is completely assembled but you may want to make a last minute check of the system before turning it on. Make sure all cables are properly connected and that all devices are properly seated or screwed in, you may want to leave the case cover off when turning the PC on for the first time just in case something isn’t connected correctly. If you hear any beeps this will indicate that something is not correctly connected or seated.
Congratulations you can now feel the satisfaction from having put your own PC together.


